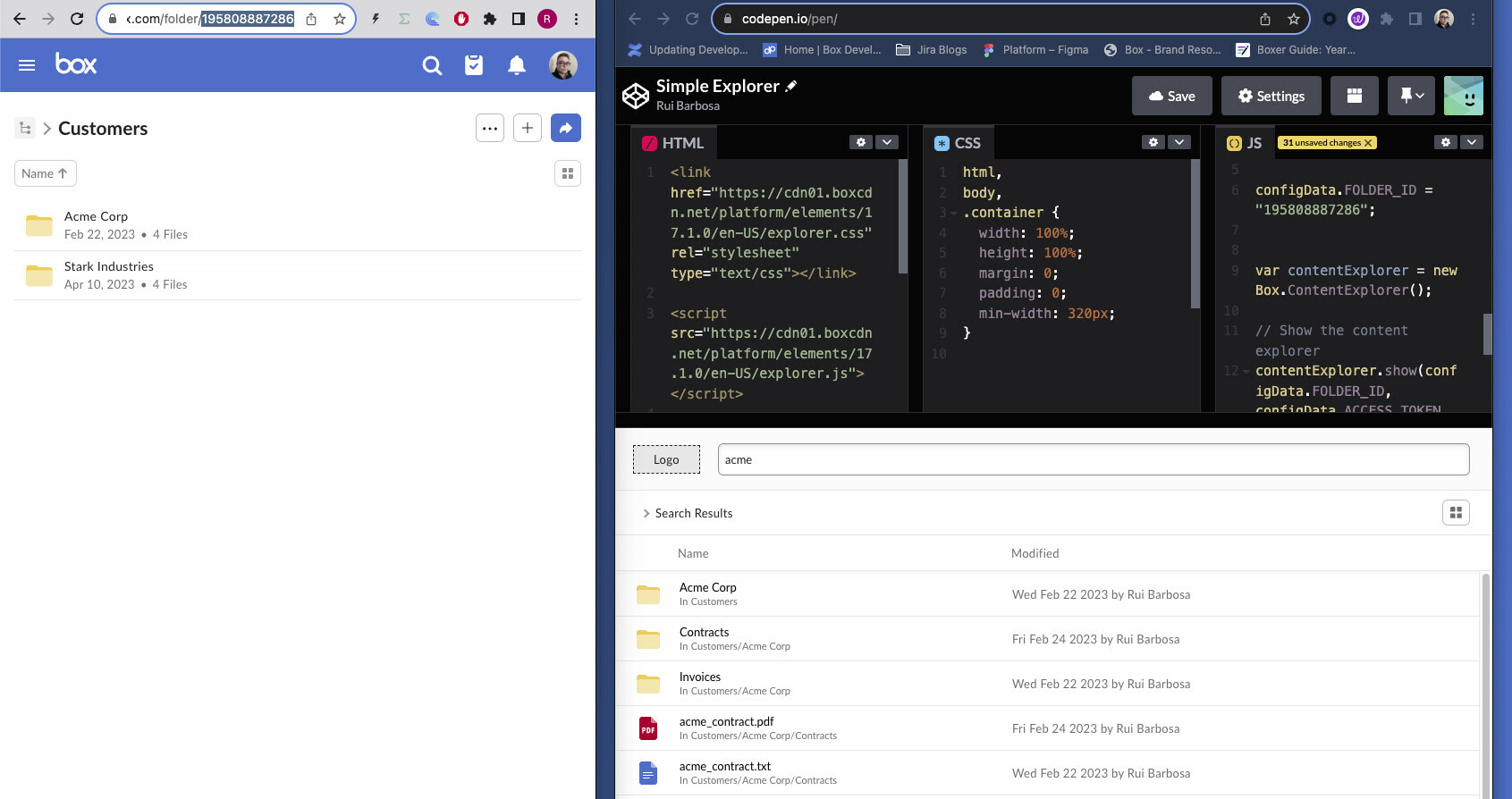
While searching on widget i am getting the following error,

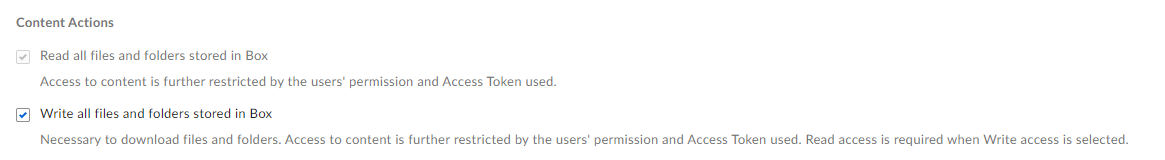
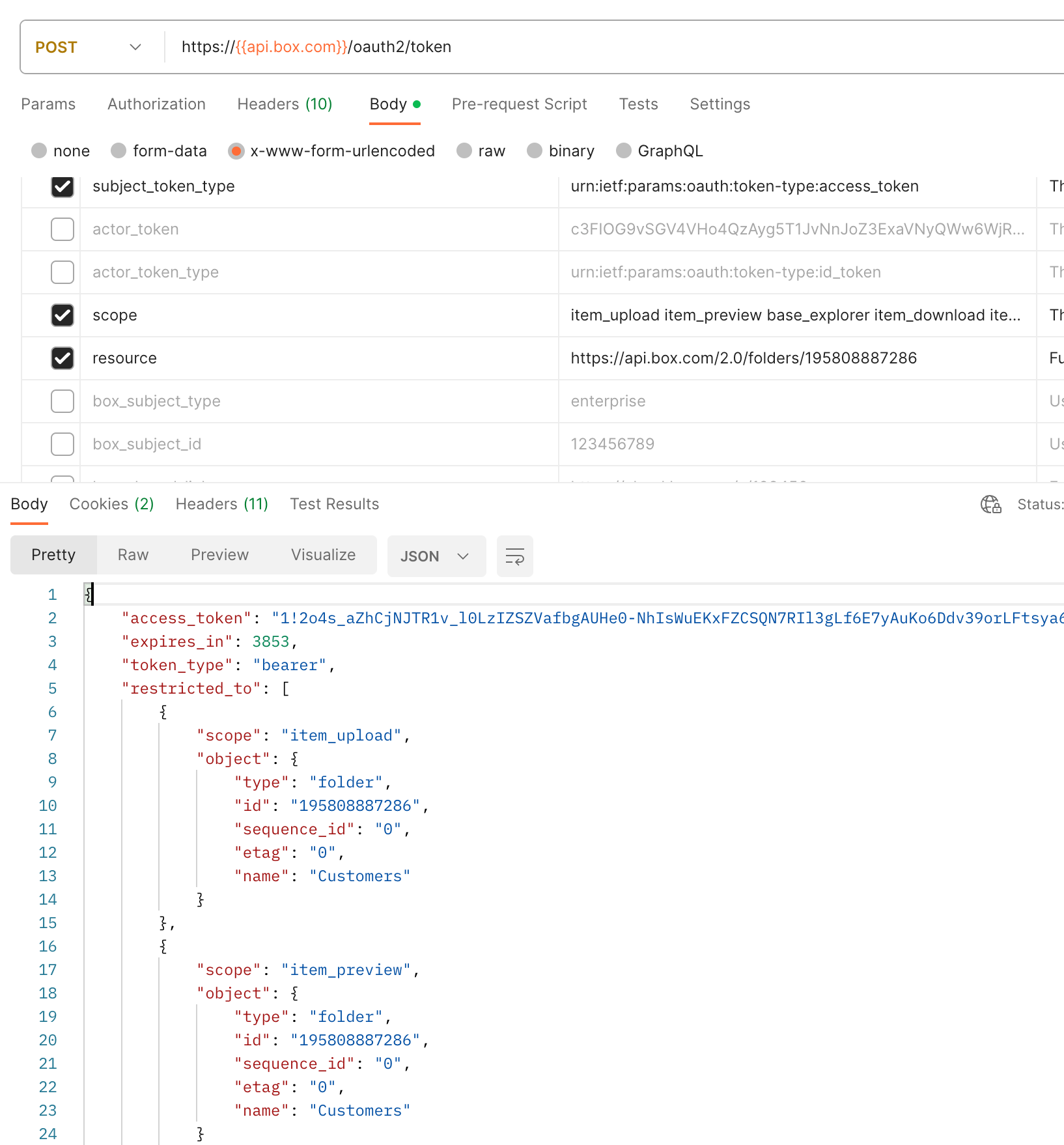
I have provided the following scopes using Java SDK while generating downscoped token.
“base_explorer”, “item_preview”,“item_download”,“item_rename”,“item_delete”,“item_upload”.
I don’t see any more scope that needs to be added to downscoped token for Content explorer widget’s search functionality.