Hi
I’m currently developing an application for my research group that pulls our images from box and applies certain operations on those images to generate training data for our CV models.
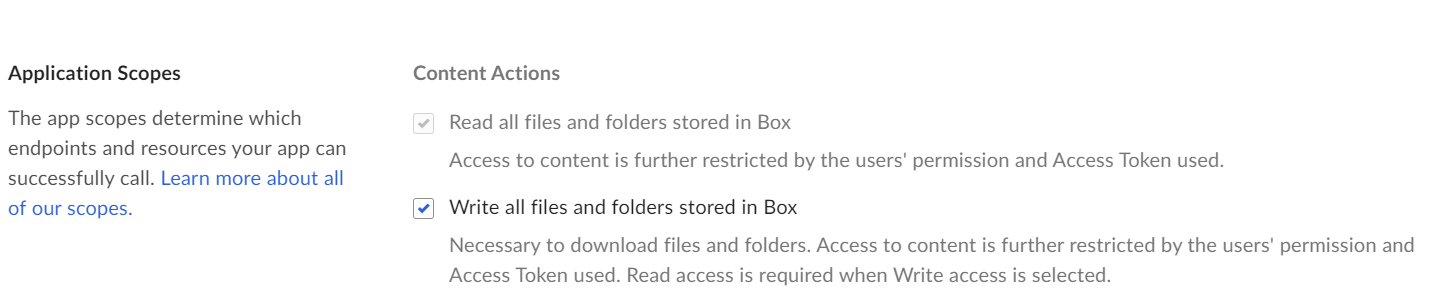
We want to make this application public through a repository, and we want users to be able to access our image data using JWT authentication (config file for authentication will be provided in the repository). However, we don’t want users to be able to write to the folders and change their image content.
I thought of giving ReadOnly permissions, however, box developer console says write permissions are required to allow users to download the content.
Below is the code that pulls the content of the image by img_id (image id).
def download_image_from_box(self, img_id):
"""
Downloads image from Box storage
"""
# Get file and read image data into memory cache
file = self.box_client.file(img_id)
file_data = file.content()
# Decode image
src = cv2.imdecode(np.frombuffer(file_data, np.uint8), cv2.IMREAD_COLOR)
return src
Will this still work if I enable ReadOnly permissions?
Thank you!