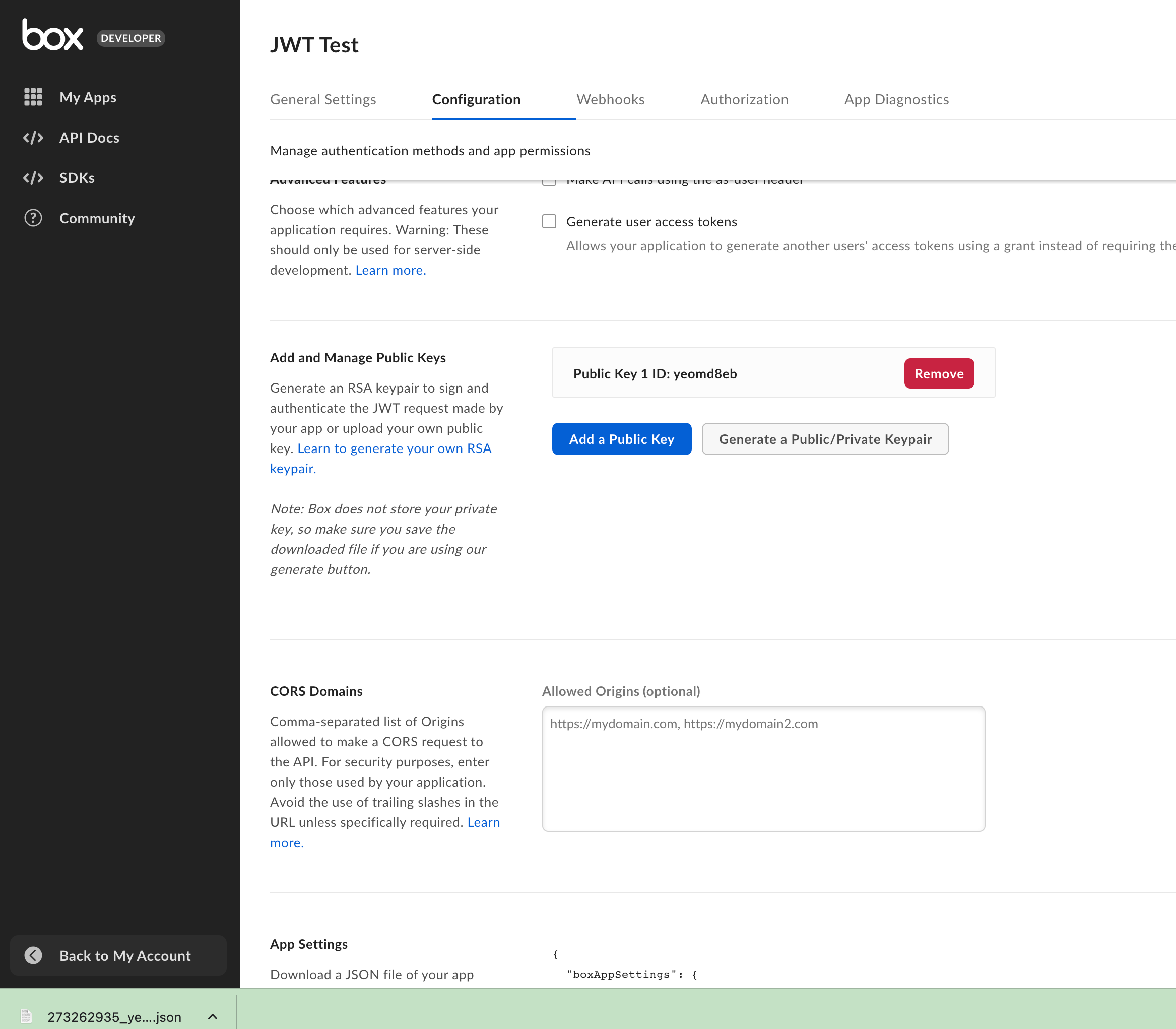
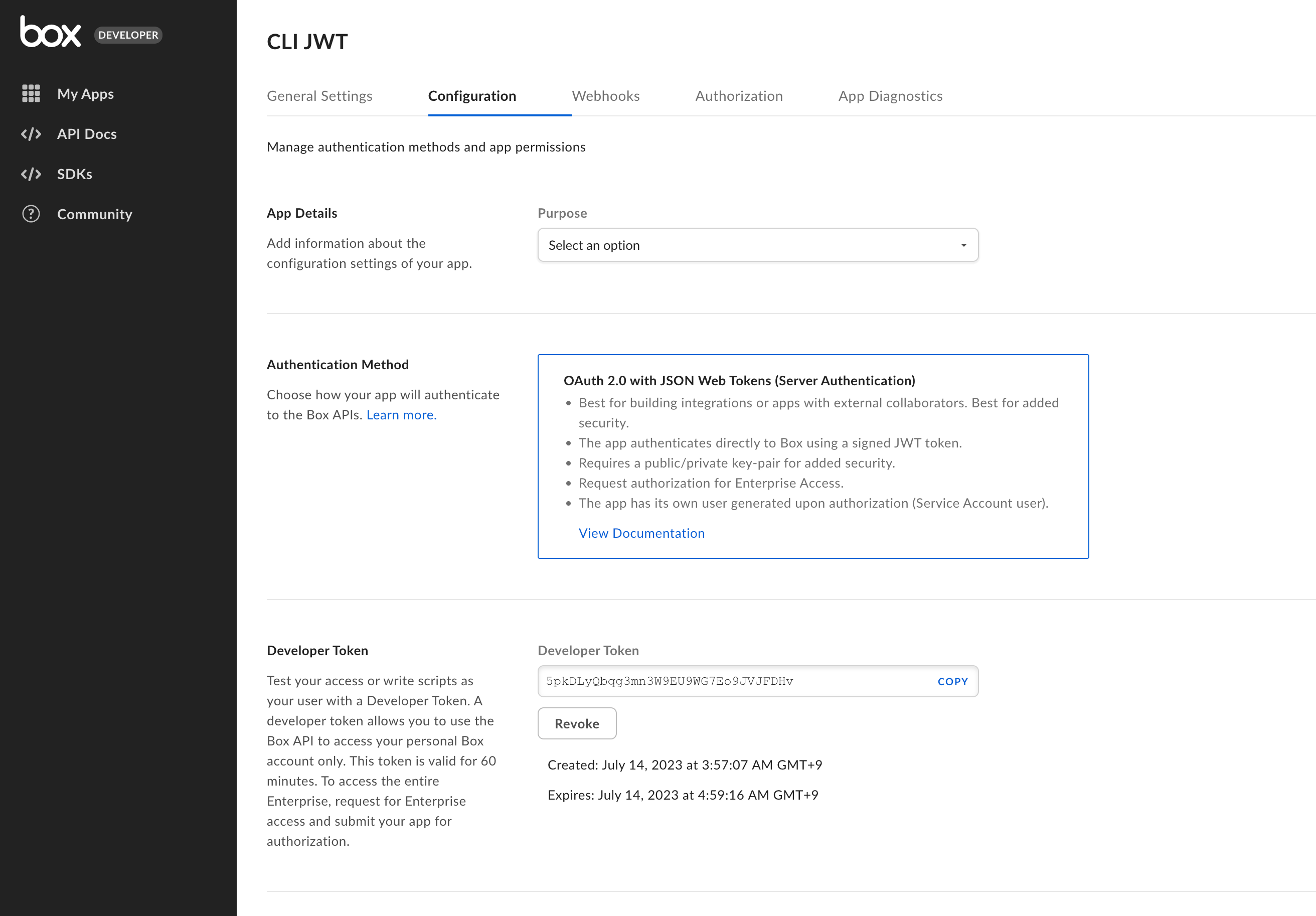
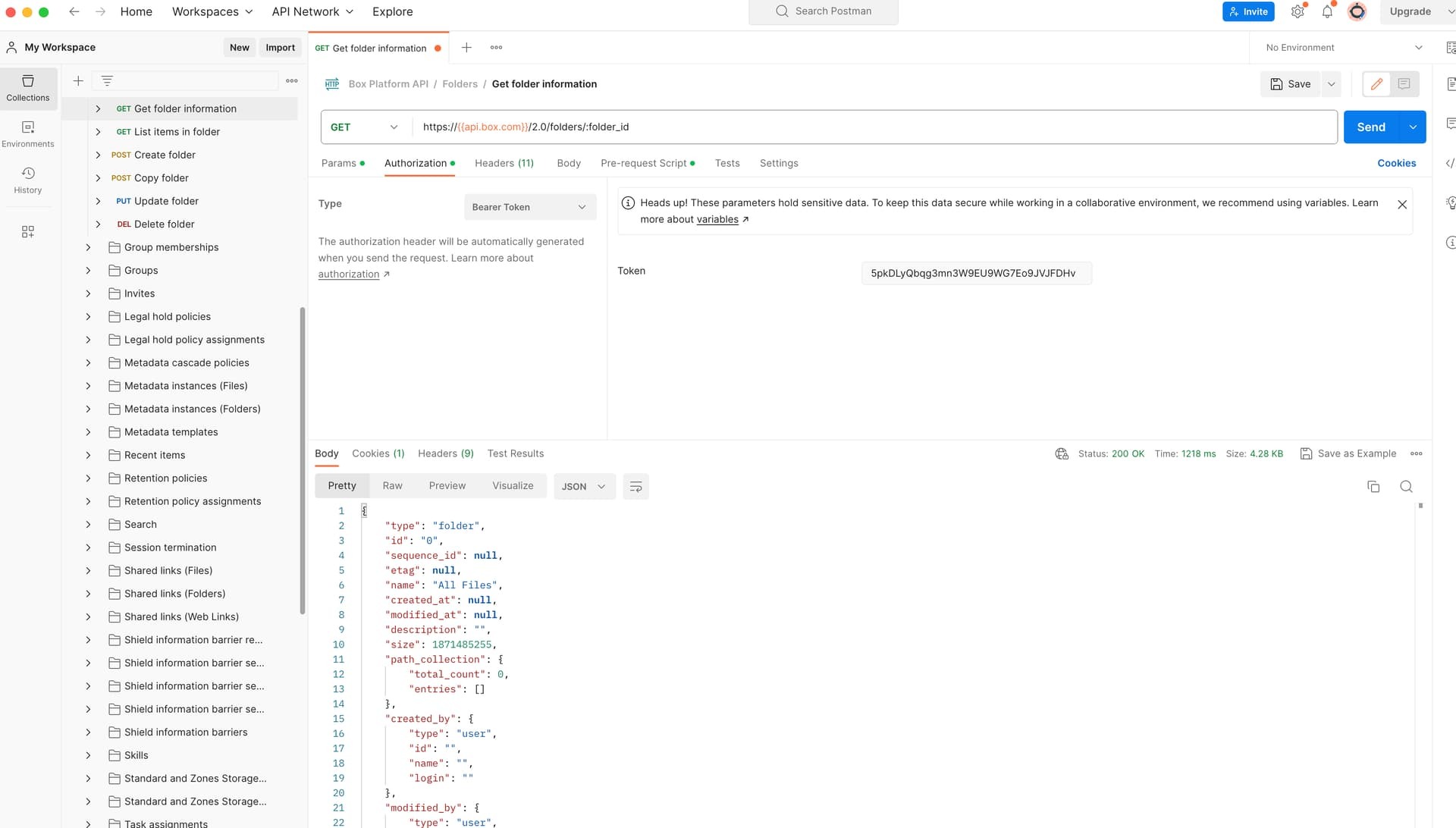
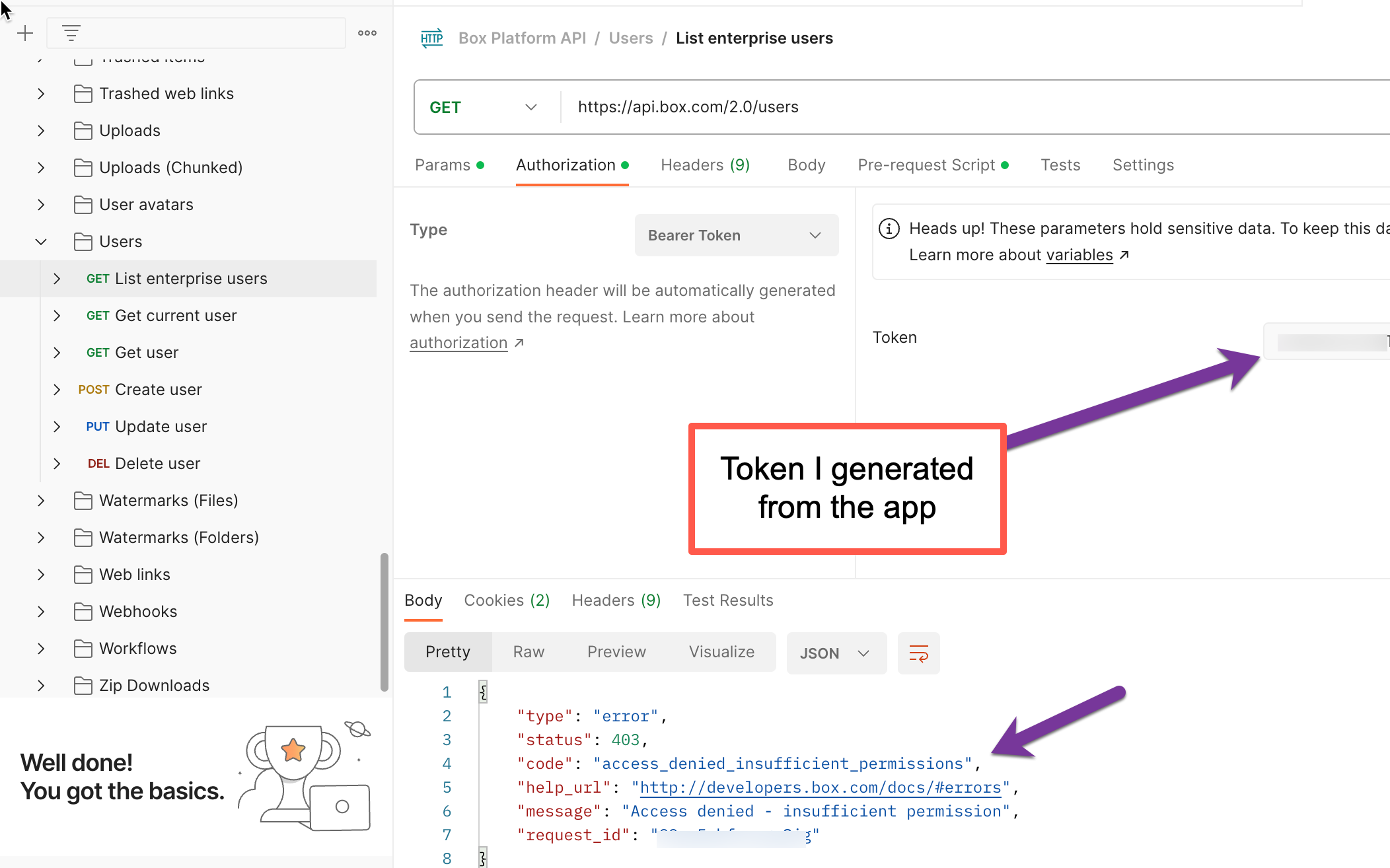
I am a ServiceNow Developer looking to build a Box Integration. Currently, I have ServiceNow configured to make API calls utilizing OAuth with JWT (Server Authentication). The steps I followed to accomplish that can be found here. This does work. For testing and development purposes I would like to configure Postman to emulate exactly what I have configured in the provided link. By that I mean I was to use the same client id, secret id, and point to the same custom app that was created in those steps. I feel like I want to use the developer token generated from the custom app to accomplish this, similar to what Alex responded within this post, however, I don’t see how to point to my custom app. Admittedly, when searching for documentation on how to accomplish this I probably don’t know enough about this process to find the correct steps. Any guidance on how to accomplish this would be appreciated.
Thank you