I am using trial version of Enterprise Box and I have created Box Custom application (authorized by Box admin). Then I generated a private key PK for that Box application and I use this PK to connect to Box App from AWS Kendra. I use Kendra Developer Edition in this test.
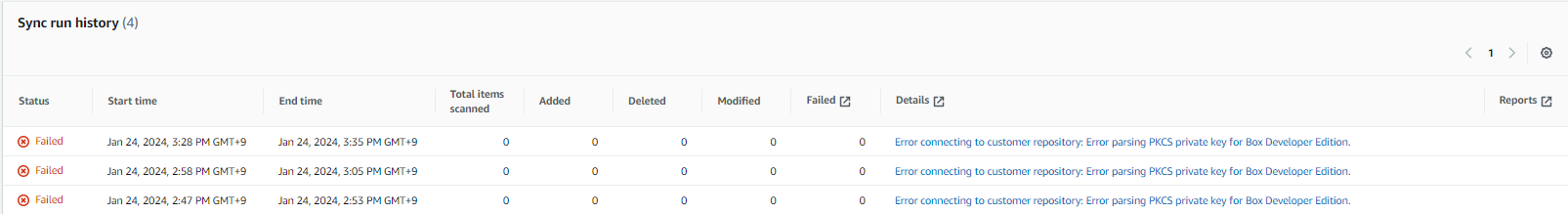
This method used to work, however today I received the below connection error after providing new PK to Kendra. PK is passed to Kendra using Secrets Manager.
Error connecting to customer repository: Error parsing PKCS private key for Box Developer Edition.
I made sure the PK is copied properly to Kendra. I also tested connectivity using the same PK and Box SDK and I can connect successfully to Box App programmatically using Python, however the connection from AWS Console fails.
What can cause this error?
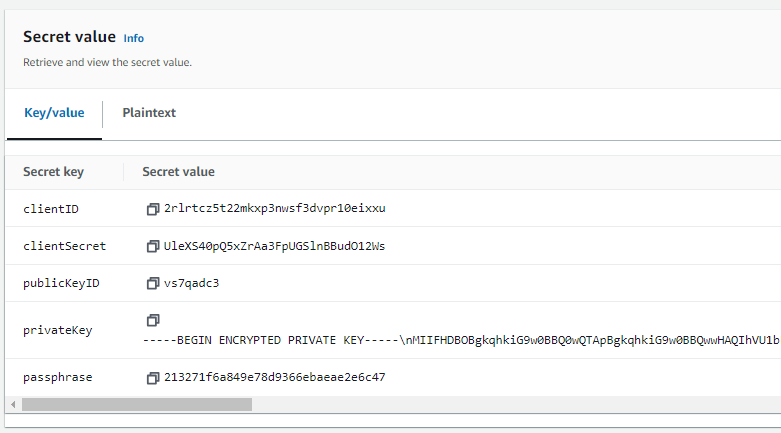
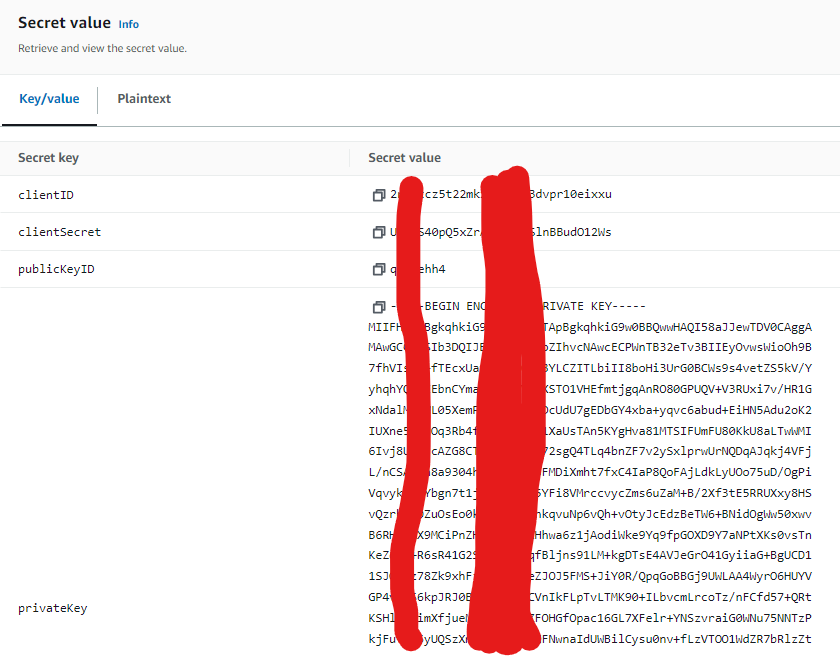
This is private key format generated from BOX Application. It contains “\n” character as text. I normally copy “privateKey” into secret in Secrets Manager Kendra uses and this used to work.
{
"boxAppSettings": {
"clientID": "2rlrtiu5t22mkxp3nwsf3dvpr10eixxu",
"clientSecret": "UtrXS40pQ5xZrAa3FpUGSlnBBudO12Ws",
"appAuth": {
"publicKeyID": "vs8qadc3",
"privateKey": "-----BEGIN ENCRYPTED PRIVATE KEY-----\nMIIFHDBOBgkqhkiG9w0BBQ0wQTApBgkqhkiG9w0BBQwwHAQIhVU1bLSvgl8CAggA\nMAwGCCqGSIb3DQIJBQAwFAYIKoZIhvcNAwcECJ0m3yAKcUwpBIIEyKXKY3BVdPEU\noV0Ggy7XwLAyOTVbeiH+9amokZipHJdsvDT8DMDIawZsi/SATmWPqniJZjJgv0NC\n4Ao6xX5xRdqWbEUIw/ALfGje0m2XVu1ciZwApwDCIAR+ftd8DGEERJlGgV+7nqnm\nCTjuvXfj/rVBopLpL1XJ+I9esAvckLGc3t5UkR9NY0vHzDqsJ72Gsq1wj+uR2DTl\n8P2rwFDhhdhbQyWKr01FHmvNIsP1rHvLhG6/wcpiG+8CGcq/OX3vyZuUSO0rFPIL\n48iZvfh8bLwVllKuDSpdnj7xHlRF9KRmsgnSQ7wD1Rf5sshoMdltQMEp2nh7qstx\nG3tCSaR2tP8mf8MT5fUzTBCpjZH7rGt6YANgxIUZgwCAMMPfRxHc2zsCF+mtoSHp\nBivRSkeh7gEeA0r/OTp0RutcudejCgVJZB3EG4P+R0JDZ1Sz4Q7Vd6muSZdiSuuj\ntFiQKhTEO9J1bwr4zkYcaF4oMABTN1ak7kSdtaRlGZLyycfbU1BOzlrR9gTztRHH\nz64GvWU14BnJARp2Ub4AvOtcRqnOU6iLraf/zpy5R+zJwHXYVZJ/l7x5Qy87sSx4\n/LHTxNONZk0j5H8g/0CQEsvy1mMA85qh+Xf/itYPE3Icrm43CMK2E4yfrUbNdw4X\nvt7WUWQjDPNdaSFaiLbYLgxritki0lHu4TMYcFSJ+mkzx/EtBqDxTdpYqA5TxB0R\nuNTZ+lASgNIDUJLtMf5Jj0YAxAA+VxCXIxbR+OVWB59V1NCPmUcsixHqINKQXb0r\nx1ehZMME7xgYbR1GGuSIWF2RxiXUovqMQCZD3ahtSTQovOvElaZJ/6B0T87TzXtY\n+wYeVNShWIBA55NIWbMvsV4Eo0EcQTt419A38iBT4Ds5LI3SXHQHIbOOK4i/cGuW\nXm2Zk2l9waeSk5ZSNVxiurUsaxsv6bqJD96Q5Sc3AFepL8+D4VuCCzeJ3f3oBeMo\nXTQ1QXI2GaDAdI6uSwnj4FsWD9hjztv5b6cipujvz3yJGvZscLGwlKOv9ozb8mUB\nyYYecMZ72CVQgdHFPjOIE2qUKgTXEJO80eZAebSDZ0SlyJHTCDUqTCbZ0kz5Nu7v\nILd041HfnqfyPItz5HR58KHjHduyFHnFFOupKbz2tcAJ9Vm1lf8YAiKFN57V7J1N\nuFIRqSf/yVR64W2V2vUl55KUt8jE5dGKrKZifUCY1W52LUr6r+scFdcYG0Joeb1i\nduKjYtXWWKVrgVcYeYAAD+VmgJ/VrbnuXrraXViibqzg6ScELNh6eJGrEHtbC5NB\ntSzRsPQvni1yuWlvnLaCG8QVA1RKlKYTUjR+X1NQGngzqpiCVgeEXAoMn/Mna4g0\nbISqY/RXZ9V/H3Ux/UoQmqktjIHdkfo18dpP7rtsLNvUobkdLF71Kgf67AosW4dq\nFChliTTkhr2L8Rwmfyq4PUQeov6QCfSMROaZ43woZJO75gJiFh1VcJyUV0+DWSLg\nzudVAvL8HvCH04djyWzVIdS0zC00bg086rWajDO2hqWJ2aNVNnbJX6uEM67wmCJW\nPXID7YcZsgCzzK0vg/WvFSNXqot0tsWhErH4tTezi6SD069UiV6Uuvb210ec6RWc\n6azMGCHf0q2skks79+e6UQ==\n-----END ENCRYPTED PRIVATE KEY-----\n",
"passphrase": "213271f6a649e78d9366ebaeae2e6c47"
}
},
"enterpriseID": "7630518952"
}
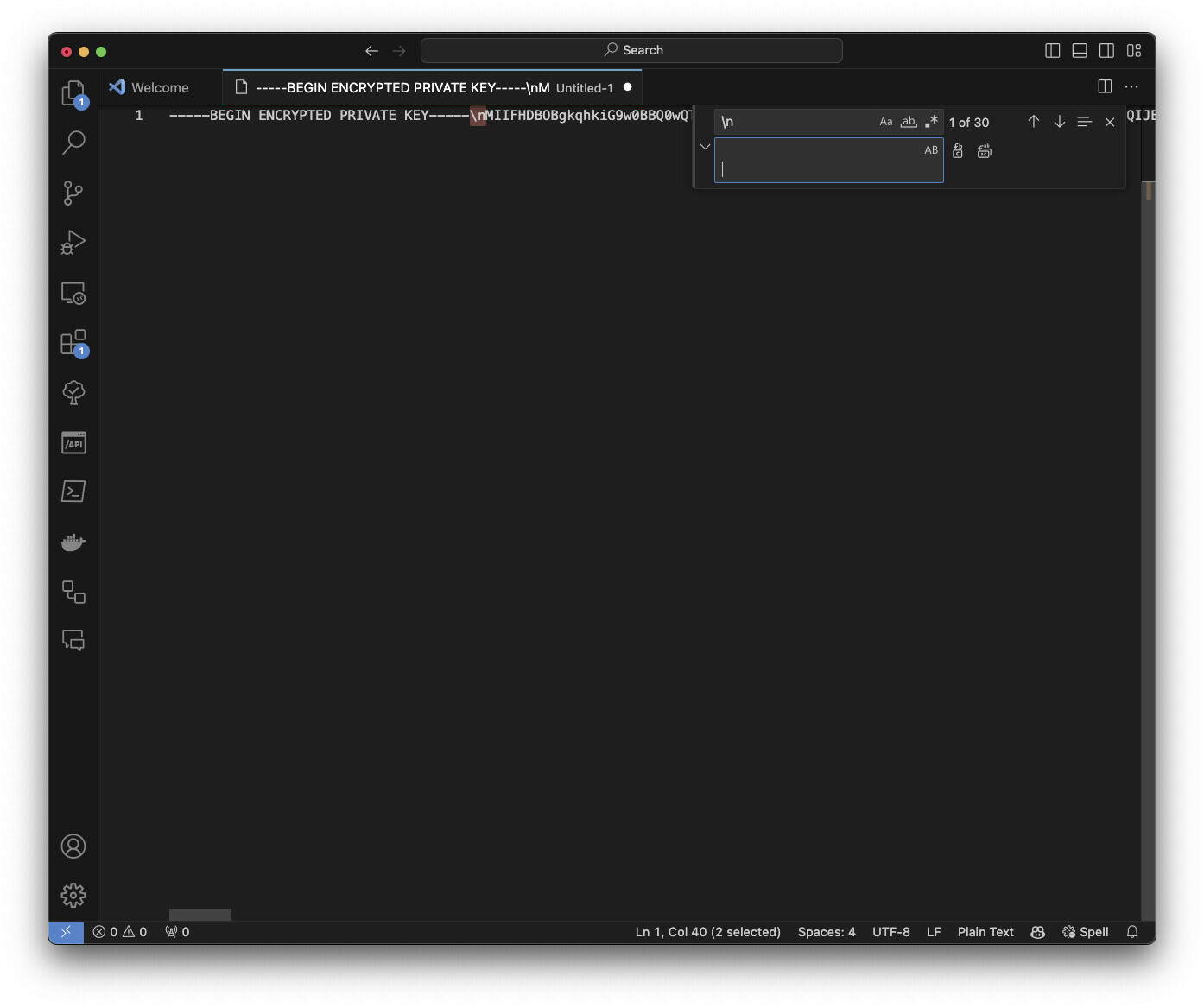
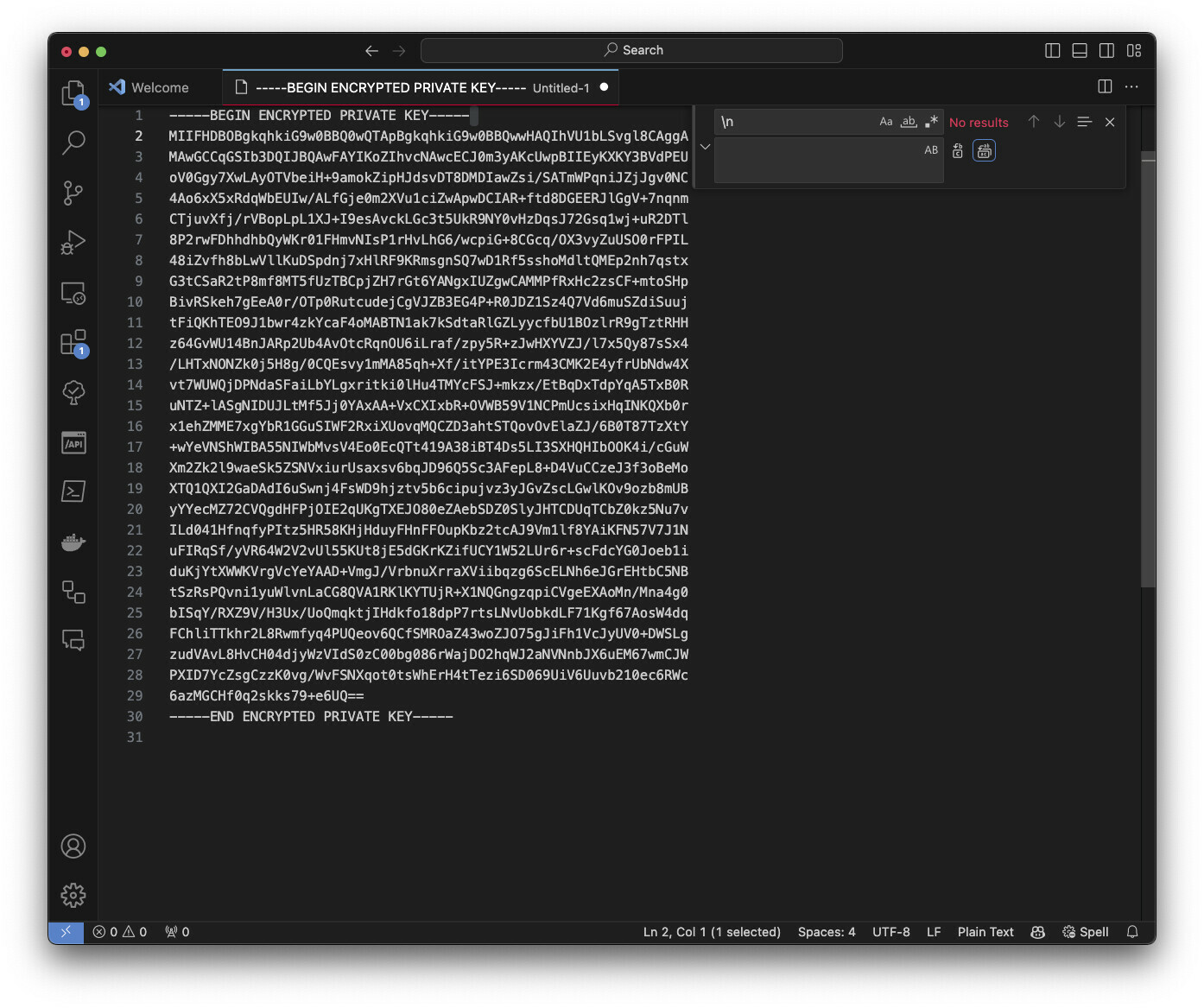
I tested various formats of this private key with “\n”, without “\n”, “\n” replaced with space, copy as “plain text” in Secrets Manager. All attempts ended with the same error - can not parse PKCS.
0
Post actions